Cybersecurity in EV Charging – Securing India’s Digital EV Infrastructure

Just this January, Arjun – a charge point Operator (CPO) in Delhi – grew his network of chargers exponentially. India has seen EVs move from a fascination of the tech savvy to mainstream vehicles as 2 million electric vehicles were sold in FY 2024-25 alone. Today there are 4.5 million EVs on the road and NITI Aayog projects 50 million EVs by 2030. This requires massive infrastructure and Arjun, rightly, took advantage of this opportunity.
The EV Charger is now a Digital Hub
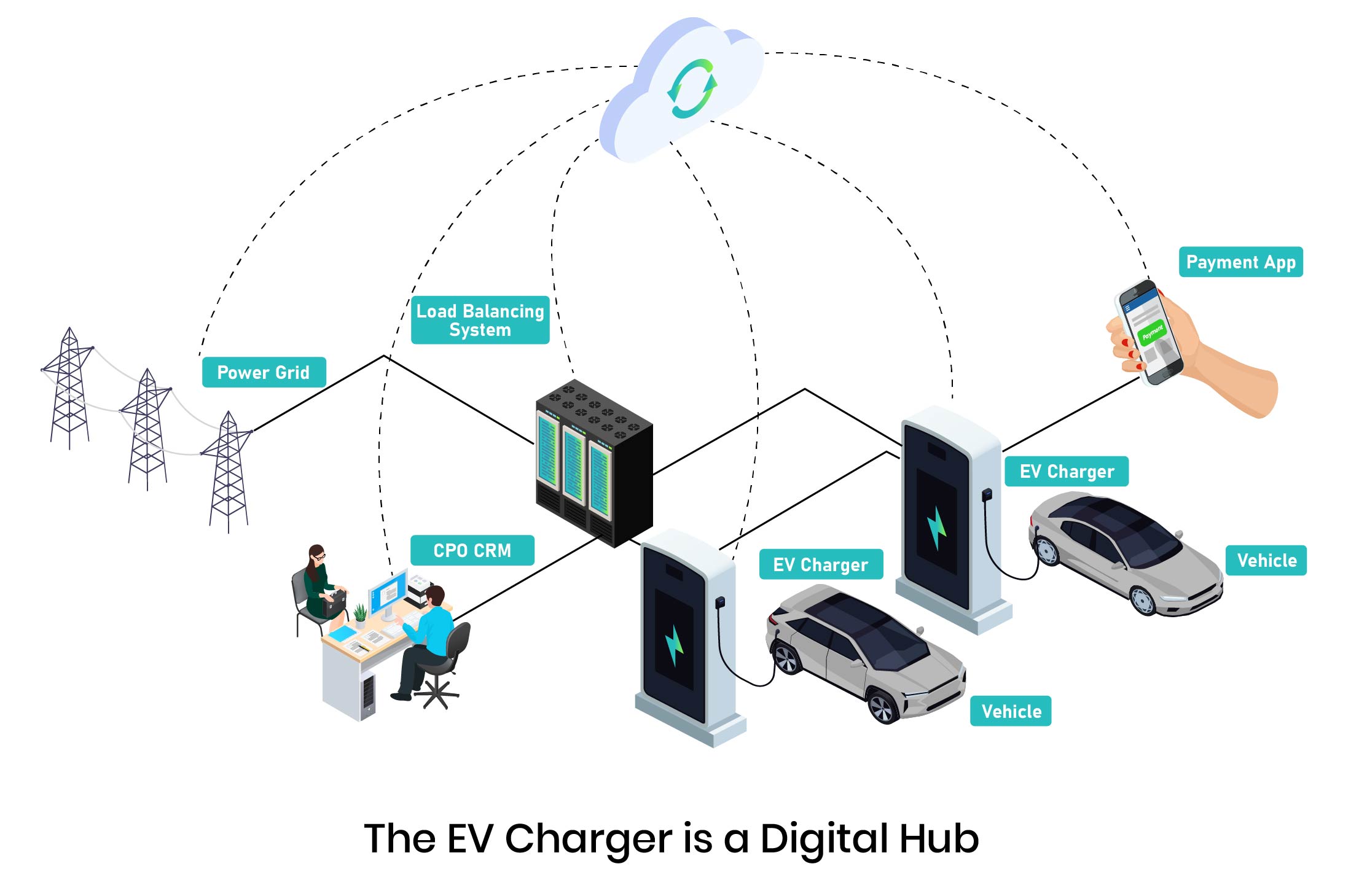
Arjun has put in a lot of chargers, started working with a lot of customers and variety of automobiles. This increased complexity and to be profitable – he started installing intelligent systems. He considered BMS (Battery Management Systems), Load Balancing and all the cool smart technologies that are helping make charge points profitable by optimizing usage and reducing waste.
But hold on… What made his centres connected and intelligent, also let him to being exposed to breakdown and cyberattacks. Rising utilization, network exposure and device incompatibility exposed the risk of hardware failure, and "handshake" errors with the central management system (CMS). There was a risk of quality dipping and device reboots – leading to precious missing of revenues. The charging was no longer just an electrical act—it had become a digital interaction and the charger connects in real-time as a digital hub with:
- The Vehicle (BMS and Onboard Computer): The Battery Management System (BMS) communicates critical limits to the charger via CAN bus or PLC.
- The Load Balancing System (for local power optimization)
- The Payment System (Gateways and User Apps): Payment gateways and authentication tokens allow access.
- The Charge Point Operator’s (CPO) Customer System: The charger sends heartbeat signals and transaction logs to the cloud via OCPP (Open Charge Point Protocol).
- The Power Grid (via Smart Metering): Smart chargers’ interface with load management systems to balance local power demand.
In this exposed connected network - Can CPOs be safe? Is there some way that they can navigate all these complexities and make use of intelligent systems without the risk of shutdown or sabotage. Let’s Explore.
Digital Complexity leads to Cyber-Risks
The rising complexity of the EV charging stack is creating problems and each node introduces dependencies Many of these systems today are imported and incompatible. Some are black boxes whose logic and maintenance are not understood. When disparate systems do not synchronize perfectly, availability drop and security risks come up. Three challenges exist:
1. Device-Level Inconsistency:
Different manufacturers using different controller logic andcreate these problems
- Weak Firmware Architecture: Low-cost chargers often utilize generic controllers with open debug ports, allowing unauthorized physical access.
- Insecure Communication: Many legacy deployments still use old standards, leaving transaction data vulnerable to interception.
- Certificate Mismanagement: As ISO 15118 adoption grows, inconsistent handling of digital certificates causes valid vehicles to be rejected.
- Supply Chain Opacity: Imported unit soften run "black box" firmware where the CPO has no visibility intopotential backdoors or dormant vulnerabilities.
2. Vehicle-Level Variance:
Different BMS protocols (proprietary vs. standard) attempting to "handshake" with the charger and lead to poor connections – risking delayed charging, or potentially hampering battery life.
3. Payment & Network Fragmentation:
Multiple apps, RFID standards, and backend protocols exist,leading to high friction in customer experience for payments.
Complexity led inconsistency leads to Cyber-risks in deployments
Operational models show clear friction when CPOs rely on fragmented hardware-software stacks. Two different risks and costs come up:
Risk 1: Inconsistency Leading to Revenue Loss
Non-standardized software handshakes break charging sessions losing revenue and customer satisfaction.
Risk 2: Malicious Attacks and Malware
Malicious malware rides charger’s network connections exposing CPO’s business to attackers.
Cyber-risks end up creating real losses
These losses are not just monetary; they can severely risk to reputation and critical services.
- $22.5 billion was lost in 2024 alone, driven by cyberattacks, ransomware and data breaches on the automotive and connected infrastructure sector cost an estimated
- Reputational damage can be caused as chargers are public screens. The Russian Display Hack with political messages was one such example
- Grid attacks can lead to brownouts. Researchers demonstrated that a botnet of compromised high-capacity chargers could be switched on/off to destabilize the local
These risks are caused by non-standardization
The root cause of these risks is the number of "unknowns" introduced by incompatible linkages. Below is a breakdown of where non-standardization creates entry points for failure or attack.
Chart 1: Areas of Potential Non-Standardization in the Charging Stack
Since the charging flow is a rigorous negotiation of Handshake → Capability Exchange → Real-Time Regulation → Termination, it’s the job of the BMS to dictate safe voltage and current limits. A corrupted data exchange could theoretically over-deliver current, risking battery health. The solution is - clean, authenticated communication from a stable integrated set of firmware. And this is where Standards come in.
The role of standards is to fix these Inconsistencies
To overcome complexity due to inconsistencies, the industry is moving toward rigorous standards. These standards address these inconsistencies better than riskier older protocols.
Chart 2: Evolution of Standards vs. Security Risks
However, the adoption in India is uneven.
- OCPP Adoption: The majority of India’s operates on OCPP 1.6, often without security extensions.
- ISO 15118: Adoption in India is nascent but critical for the next phase
- Regulatory Framework: The Bureau of Indian Standards advisory compliance remains a patchwork across unorganized players.
Compliance alone does not guarantee security. It creates a floor, but operational resilience requires a ceiling built on integrated design.
Beyond standards CPOs face operational challenges
Integration of multi-vendor fleets, and varying chargers, creating a huge integration burden on CPOs. This requires patchwork management, overcoming dependency risks, enabling network hygiene and the complex balance between stability and security.
- Integrating a patchwork of chargers. Each charger may use a different firmware version and have its own update schedule, making management complicated.
- Dependency Risks: If a security problem is found, it can take a long time to get fixes, leading to extended downtime.
- Network Hygiene: Securing on-ground networking at semi-public sites (malls, housing societies) is difficult when chargers lack internal firewalls.
- Stability vs. Security: CPOs often hesitate to patch devices because updates that are not properly tested can cause chargers to stop working, requiring expensive site visits.
This is where an ecosystem that integrate all these standard and operational factors is necessary – One that Exicom has come up with.
An Integrated Exicom Ecosystem Neutralizes Cyber-Risks
Exicom’s pioneering approach to rests on its integrated architecture, by controlling the in-house OS and firmware, Exicom reduces the unknowns that impacts todays deployments of EV chargers in Indian Charge Points. .
In an integrated system, the charger is not a patchwork of components. Exicom designs the Hardware, the Controller, the Firmware, and the Operating System as a unified stack.
- Eliminating the "Black Box": Because the firmware is developed in-house, there are no hidden backdoors from third-party suppliers. Security patches can be verified and deployed instantly across the fleet.
- Standardized Handshakes: The system is pre-calibrated to handle the nuances of Indian grid fluctuations and diverse EV models, significantly reducing "inconsistency" errors that lead to revenue loss.
- Secure Boot & Chain of Trust: The integrated architecture ensures that the charger will only boot up if the software signature matches the authorized Exicom key. This prevents malware from taking root, even if a physical port is tampered with.
The approach also ensures efficiency measures that stabilize daily operation such as
- Regular OTA Updates: Shift from manual updates to automated, secure Over-The-Air (OTA) campaigns using signed packages.
- Certificate Lifecycle Management: Automate the rotation of authentication tokens to prevent service denials due to expired credentials.
- Network Segmentation: Isolate chargers on private APNs (Access Point Names) rather than the public internet to reduce attack surface.
- Deployment Checklists: Standardize installation protocols to ensure physical ports are locked and default passwords are changed immediately.
- Device Health Monitoring: Use agentic-like monitoring to detect anomalies in heartbeat patterns, catching malfunctions before they become outages.
As India races toward its 2030 target of 50 million EVs, the charging network will become as critical as the banking networks. This EV Charging infrastructure has to be secure and stable – not just efficient and profitable. By shifting from assembled components to integrated, secure-by-design ecosystems, CPOs can ensure that their chargers remain assets that generate revenue, rather than liabilities that generate risk.
Bibliography:
Frequently Asked Questions
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse.





.jpg)

